Category: Security
Network security consists of the provisions made in an underlying computer
 |
network infrastructure, policies adopted by the network administrator to protect the network and the network-accessible resources from unauthorized access and consistent and continuous monitoring and measurement of its effectiveness (or lack) combined together.
vSEC:CMS and Yubikey
Very good video clip for Versasec and Yubico services.
Fortigate Debug Tips
https://kb.fortinet.com/kb/documentLink.do?externalID=FD33882
Tenable Essential deployment and Tips
Tenable Essential is a free vulnerability tool in the market. It only supports 16 hosts of small or lab environment. We downloaded the VM version…
Why Tenable/NESSUS requires full level 15 access for Cisco devices? Don’t need it.
It is a long battle between vulnerability scanner vendors and network engineers to allow level 15 access privilege from the scanner. Since it is common…
SSL/TSL Encryption and certificate 101
Good site to understand how SSL works~ SSL/TSL handshark There are many tutorials and video how to SSL/TLS HTTPS protocol is working, but below video is…
How to install a certificate for PRTG server
Generate a CSR 1. Download and install OpenSSL (Windows version) at PRTG server. 2. Generate CSR for Microsoft CA C:\OpenSSL-Win32\bin>openssl req -nodes –newkey rsa:2048 –keyout…
[Sophos UTM9] SnapChat text is not working on iPhone
I have installed the Sophos UTM9 firewall that released for home use only. This firewall is pretty good. Actually, the firewall is one of the…
How to enable SSH on ASA5505 thru WAN/Outside interface
Here is how to enable SSH on ASA5505 thru WAN interface (Outside) ASA_5505# conf t ASA_5505 (config)# enable password [Enable Password] encrypted ASA_5505 (config)#…
Windows Server 2012 as RADIUS for Cisco Router & Switch
If you have a lot of devices on your network, centralized authentication server is always handy for efficient control of devices, convenient and scalable. …
Cisco IOS Zone based Firewall configuration and Tips
Simple 6 Steps to configure Notes; Zones; Internet, Trust, WAAS and Guest Interface Serial1/0 : To the Internet Interface Gi0/0 : Trust Interface G1/0…
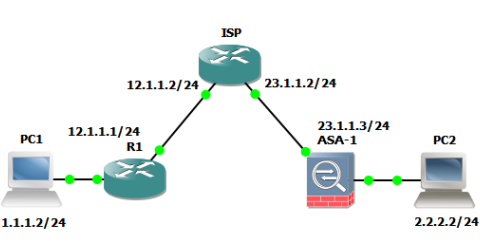
IPSec VPN between Cisco Router and ASA without NAT
Sample configuration for IPSec VPN between Cisco Router and ASA 5520 ver8.4 without NAT. Notes; R1 : Cisco 3745 ver. 12.4(15)T14 ASA : Cisco…
How Cryptography and PKI and SSL work?
This is quick, basic and fundamental idea about Encryption method. 1. Encryption with Key system Encryption : Hiding what is sent from on node…



 The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.
The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.

![[Splunk] – Basic search fields and commands logo_splunk.png](https://ipbalance.com/wp-content/uploads/2009/06/logo_splunk-100x80.png)

Recent Comments