Category: Security General
vSEC:CMS and Yubikey
Very good video clip for Versasec and Yubico services.
Tenable Essential deployment and Tips
Tenable Essential is a free vulnerability tool in the market. It only supports 16 hosts of small or lab environment. We downloaded the VM version…
How Cryptography and PKI and SSL work?
This is quick, basic and fundamental idea about Encryption method. 1. Encryption with Key system Encryption : Hiding what is sent from on node…
Password changer for Windows System.
Tweet Here is steps for how to change a system passwords. A. Download(buy) tools from www.password-changer.com. – Less than $40, it is reasonable price. VS…
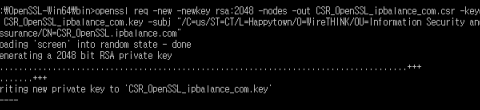
How to create CSR (Certificate Signing Request) with OpenSSL
Here is How to create a CSR (Certificate Signing Request) with OpenSSL. Check "How to verify a certificate thru OCSP responder with Free tool OpenSSL"…
How to verify a certificate thru OCSP responder with Free tool OpenSSL
To verify a certificates thru OCSP responder is more demanding in these days and here is simple steps to test OCSP responder from your network…
How to configure CoPP (template) on Cisco devices
CoPP (Control Plane Policying) should be used to protect RP on the Cisco devices by unnecessary and malicious traffic. The traffic managed by the RP(Route…
How to allow Traceroute and TraceRT on Access-list(ACL)
Here is the sample configuration to allow traceroute(Unix or Network devices) and tracert(MS Windows) "TraceRoute" commands of Unix and Cisco devices send UDP packets, while…
Security Warning – Exposed WAN Link Identity by reverse lookup
If someone knows what is your IP address of WAN link, if someone knows what ISP you are currently using, if someone knows where your…
How to configure Pix 515 for connecting PDM
This is a quick guide for configuring Cisco PIX 515 which is discontinued model. Even though Cisco PIX 515 is kinds of old model, it…
Modifying Huge ACL & prefix- list ?
Tweet Probably, there are multiple way to achieve your goal. Here is one of simple way that I knew and used in my work. (using…
Preventing Security Attacks from all OSI 7 Layer
Tweet Let’s quickly look what kinds of Security Attacks on OSI 7 Layer. Layer 7. Application /6. Presentation/5. Session Layer – Virus, Warms, Tro-hourse, Buffer…



 The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.
The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.

![[Splunk] – Basic search fields and commands logo_splunk.png](https://ipbalance.com/wp-content/uploads/2009/06/logo_splunk-100x80.png)

Recent Comments