Sample configuration for IPSec VPN between Cisco Router and ASA 5520 ver8.4 without NAT.
Notes;
R1 : Cisco 3745 ver. 12.4(15)T14
ASA : Cisco ASA 5520 ver. 8.4
GNS3 : Ver. 1.2.1
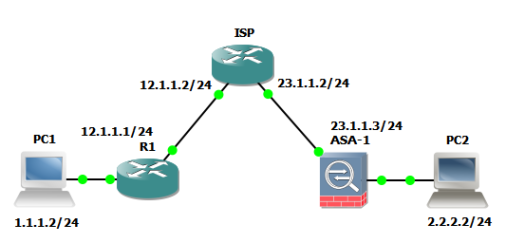
1. ASA configuration
1-1. isakmp(ikev1) Policy
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha (Default)
group 2
lifetime 86400
1-2. isakmp(ikev1) key & Tunnel
tunnel-group 12.1.1.1 type ipsec-l2l
tunnel-group 12.1.1.1 ipsec-attributes
ikev1 pre-shared-key *****
1-3. ACL
access-list VPN extended permit ip 2.2.2.0 255.255.255.0 1.1.1.0 255.255.255.0
1-4. IPSec Transform
crypto ipsec ikev1 transform-set TS esp-aes-256
1-5. Crypto MAP
crypto map VPN 1 match address ACL_VPN
crypto map VPN 1 set peer 12.1.1.1
crypto map VPN 1 set ikev1 transform-set TS
1-6. Apply Crypto MAP to Interface
crypto map VPN interface outside
1-7. Enable isakmp. ; It might be as default
crypto ikev1 enable outside
1-8. Default route
route outside 0.0.0.0 0.0.0.0 23.1.1.2
1-9. Useful commands
show run ip address
show ip
show nameif
show run timeout
show traffic
show perfmon
show arp
show route
2. Router configuration
2-1. isakmp(ikev1) Policy
crypto isakmp policy 1
encr aes 256
authentication pre-share
group 2
hash sha (Default)
2-2. isakmp(ikev1) key
crypto isakmp key HELLO address 23.1.1.3
crypto isakmp keepalive 60 60
2-3. ACL
access-list 100 permit ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
2-4. IPSec Transform
crypto ipsec transform-set TS esp-aes 256 esp-sha-hmac
2-5. Crypto MAP
crypto map VPN 1 ipsec-isakmp
description VPN
set peer 23.1.1.3
set transform-set TS
match address 100
2-6. Apply Crypto MAP to Interface
interface FastEthernet0/0
ip address 12.1.1.1 255.255.255.0
duplex auto
speed auto
crypto map VPN
2-7. Useful commands
show crypto isakmp sa
show crypto ipsec sa
clear crypto isakmp sa ; terminate VPN manually
clear ipsec sa peer [ peer IP ]
clear crypto ikev1 sa [ peer IP ]
clear crypto sa counters [ peer IP ]
3. Troubleshooting & Tips
3-1. Connectivity
; Make sure network connectivity between outside IP / interfaces.
If you see error message " ISAKMP:(0): retransmitting phase 1 MM_NO_STATE… "
from debug crypto isakmp on Router, it indicated some connectivity issue. Check default route of ikev1 enable on outside of interface on ASA side.
3-2. Debug command
For Cisco Router
debug crypto isakmp
debug crypto ipsec
debug crypto condition peer [ peer IP ]
For Cisco ASA
debug crypto isakmp 150
debug crypto ipsec 150
debug crypto condition peer [ peer IP ]



 The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.
The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.

![[Splunk] – Basic search fields and commands logo_splunk.png](https://ipbalance.com/wp-content/uploads/2009/06/logo_splunk-100x80.png)
