Category: Security
Network security consists of the provisions made in an underlying computer
 |
network infrastructure, policies adopted by the network administrator to protect the network and the network-accessible resources from unauthorized access and consistent and continuous monitoring and measurement of its effectiveness (or lack) combined together.
How to configure IPSec VPN with GNS3
Here is simple steps of configuring Cisco IPSec Site-to-Site VPN. Part1 – ISAKMP(Internet Security Association Key Management System) : To establish tunnel / secure…
Basic 802.1x configuration on Cisco switch with FreeRADIUS
FreeRADIUS Server (10.10.10.10) 1. Edit "users" file root@FreeRADIUS:/etc/freeradius# pico users "Jone Wild" Cleartext-Password := "!PB@1@nce" Reply-Mesage = " Hello~ " 2….
Cisco device RADIUS configuration with Server 2008R2
Cisco device RADIUS configuration with Server 2008R2 OS : Windows 2008 R2 Standard. 4G RAM Window server is joined as domain server. IP 192.168.1.100…
Firewall rules for Apps.
Tweet Reference firewall rules for well-known Apps. KaKaoTalk Free call and video Outgoing ports(To the destination) – Signaling : Destination IP(Network) – 110.76.141.x, 23.78.190.13…
Best practice firewall setting for user FTP traffic
Tweet How you handle user FTP traffic? as you know there are two transfer modes, passive and active, for FTP traffic. – Active mode :…
Password changer for Windows System.
Tweet Here is steps for how to change a system passwords. A. Download(buy) tools from www.password-changer.com. – Less than $40, it is reasonable price. VS…
How to router TACACS authentication with loopback 0 interface
If you are using TACACS server and dedicated management network (IP), you might have loopback 0 interface on each devices that you are managing. As…
Cisco AAA configuration in security best practices
Network security is big deal! Here is best practice of how to configure Cisco AAA in most effective and practical way. Example of the…
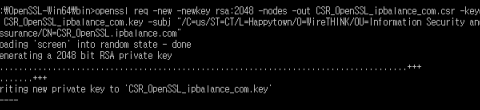
How to create CSR (Certificate Signing Request) with OpenSSL
Here is How to create a CSR (Certificate Signing Request) with OpenSSL. Check "How to verify a certificate thru OCSP responder with Free tool OpenSSL"…
How to verify a certificate thru OCSP responder with Free tool OpenSSL
To verify a certificates thru OCSP responder is more demanding in these days and here is simple steps to test OCSP responder from your network…
Why 3 MAC addresses required for Cisco port-security with VoIP phone?
Why 3 MAC addresses required for Cisco port-security with VoIP phone? In general, port-security is turned on, the default number of allowed mac-addresses is 1….
How to configure CoPP (template) on Cisco devices
CoPP (Control Plane Policying) should be used to protect RP on the Cisco devices by unnecessary and malicious traffic. The traffic managed by the RP(Route…


 The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.
The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.

![[Splunk] – Basic search fields and commands logo_splunk.png](https://ipbalance.com/wp-content/uploads/2009/06/logo_splunk-100x80.png)

Recent Comments