Author: Chris
How to convert Cisco AP521 back into stand alone mode
Tweet Are you sure you can convert Cisco AP521 Controller-based mode back to Standalone mode ? Cisco said once you convert to Standalone mode, you…
[Enterasys] How to configure Syslog server
Tweet While I was testing Splunk, I need to add more devices to Splunk index pages. This example shows how to configure Enterasys Switch to…
How to use Splunk with tips
Tweet Yes, it is expensive tool, if you attempt to use it on large network. Yes, it is not easy to use if you are…
How to configure Cisco WLC(Wireless Controller) 526?
Tweet If you are looking for reliable and powerful wireless network for your company? Budget is kinds of tight? If you are willing to spend…
Password Recovery Procedure – Tasman(Nortel)
Tweet Tasman network is now part of Nortel networks. This is a instructions to recovery Tasman router password. Manufacture login/password was tasman/tasmannet, but since Nortel…
How to install free TACACS+ on Ubuntu
Tweet Here is the simple steps to install free TACACS+ application. 1. Download TACACS+ 2. Install Free TACACS+ on Ubuntu 3. Configure tac_plus.conf 4. Testing…
Modifying Huge ACL & prefix- list ?
Tweet Probably, there are multiple way to achieve your goal. Here is one of simple way that I knew and used in my work. (using…
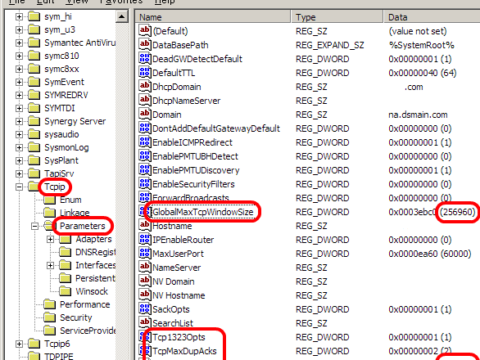
Internet Speed Issue – How to use TCP window scaling option
From few simplifying test results on previous article "Internet Speed Issue – Why TCP window size is matter", indeed TCP window size made difference of…
How to setup FreeRADIUS server?
Tweet Here is a simple documentation how to setup FreeRADIUS server. It’s written by Korean. http://www.ibm.com/developerworks/kr/library/l-radius/
Preventing Security Attacks from all OSI 7 Layer
Tweet Let’s quickly look what kinds of Security Attacks on OSI 7 Layer. Layer 7. Application /6. Presentation/5. Session Layer – Virus, Warms, Tro-hourse, Buffer…
How to hide an access-list applied?
Tweet Sometime, you even don’t want to reply ICMP unreachable message response back to requester. It’s very simple. Here is how you do it. (Assume…
Basic QoS
Tweet There are 4 priority queues: high, medium, normal, low. The default queue is the normal queue, by default. The high and medium queues…




 The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.
The www.ipBalance.com runs by a volunteer group with IT professionals and experts at least over 25 years of experience developing and troubleshooting IT in general. ipBalance.com is a free online resource that offers IT tutorials, tools, product reviews, and other resources to help you and your need.

![[Splunk] – Basic search fields and commands logo_splunk.png](https://ipbalance.com/wp-content/uploads/2009/06/logo_splunk-100x80.png)

Recent Comments